Can a hub-spoke cloud architecture help increase security and reduce costs?
- Brett Borschel
- Dec 12, 2021
- 2 min read
Updated: Dec 31, 2021
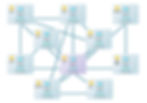
If your company is like most, your cloud probably looks like the picture above. This is to be expected unless you have mature change control procedures that are rigorously enforced to maintain a standardized network architecture.
The main problems with the full or partial cloud architecture are:
Security rules are hard to maintain - The default NSG rule being "allow any peered virtual networks" will mean almost no restrictions without adding additional restriction.
Application sprawl - Developers write code for widgets that rely on other resources, which call other databases... Who knows what the applications are actually doing when it comes time to push to the application to production? What if you are asked to move the entire workload to another cloud or back to on-prem?
Duplicate resource costs - There can be a tendency to pay for multiple app gateways, firewalls, AD servers, and databases per each virtual network when a single resource leveraged to multiple upstream networks will work.
Alternatively, using the "hub-spoke" model shared resources in the hub can be leveraged to support multiple spoke network resources saving costs, increasing security and scalability.

Services that are used for multiple spoke resources should be built in the hub and protected by NSG rules. Resources like Domain Controllers, Express Route Gateways, App Gateways, Azure Firewalls, NAT Gateways, third party NVAs, and Bastion segments should all be located in the hub network to best economize Azure service costs.
The hub-spoke model also allows for securely connecting multiple spoke networks to a shared services spoke by routing the traffic through an Azure firewall in the hub.
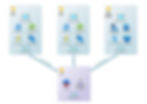
In this example, multiple development environments are given access to a shared database subscription by using user defined routes to point network traffic to the hub Azure firewall and allowed by a firewall policy rule to connect through the security appliance.
To learn more about securing hub-spoke virtual networks see this document: https://docs.microsoft.com/en-us/azure/firewall-manager/secure-hybrid-network
To learn more about Hub-Spoke reference architectures see this document: https://docs.microsoft.com/en-us/azure/architecture/reference-architectures/hybrid-networking/hub-spoke?tabs=cli
